
Accounting cybersecurity remains a growing issue in 2024. With financial data continuing to be a prime target for hackers, the urgency for accounting professionals and businesses to secure this sensitive information has never been higher. As such, IT teams and accountants must consider strategies to safeguard this previous data.
Newsletter sign up
"*" indicates required fields
In this article, we look at how accountants can structure an accounting cybersecurity strategy to keep financial data secure. We share tips to keep data secure and champion dual cyber security and accounting best practices throughout your organization. Also, we examine how cloud-based accounting software helps keep data safe and secure.
Why Accounting Cybersecurity Needs to be Top-Of-Mind
While the cloud has made accounting easier to access and manage, it’s also opened up many more threats than conventional paper-pen bookwork. To clarify, even robust IT infrastructures can be targeted and penetrated by hackers and cybercriminals. But, what’s even more disheartening and dangerous is that internal accounting data threats are even more costly.
Some think that cyber security and data security are not linked to the accounting life cycle. This isn’t true. For example, besides hacking, financial data threats can include errors and unintentional data breach that necessitates sophisticated solutions to safeguard data. Accountants and accounting firms know that financial data breaches threaten livelihood, business growth, customer relations, and more. Similarly, the same account details you use to track debits and credits are vulnerable to malware and malicious activity.
Stolen Accounting Data Can Include:
- Account numbers
- Transaction details
- Credit card numbers
- Bank accounts
- Usernames
- Passwords
- Personal and private information
Most importantly, the biggest danger is assuming that ‘my accounting firm’ or ‘my company’s financial data’ isn’t threatened. Data breaches in the financial services industry, and in general, are on the rise.
The State of Accounting Cybersecurity Attacks 2024
The shift to remote work necessitated by the COVID-19 pandemic brought with it an upsurge in cyberattacks. The landscape in 2024 shows a continuation of this trend, with a significant rise in the sophistication and number of cyberattacks. Innovations in cybersecurity measures are being met with equally advanced tactics by cybercriminals, including the emergence of Malware as a Service (MaaS) and more complex phishing techniques. These developments have made cybersecurity a dynamic field, requiring constant vigilance and adaptation.
MaaS platforms have democratized the tools necessary for launching cyberattacks, lowering the barrier for entry for potential hackers. This, coupled with the increasing use of AI in crafting extremely personalized phishing attacks using voice cloning, video deepfakes, and tailored emails, presents new challenges for accounting cybersecurity.
How does one account for the cost of these data breaches? Here’s a snapshot of the risings costs through 2023:
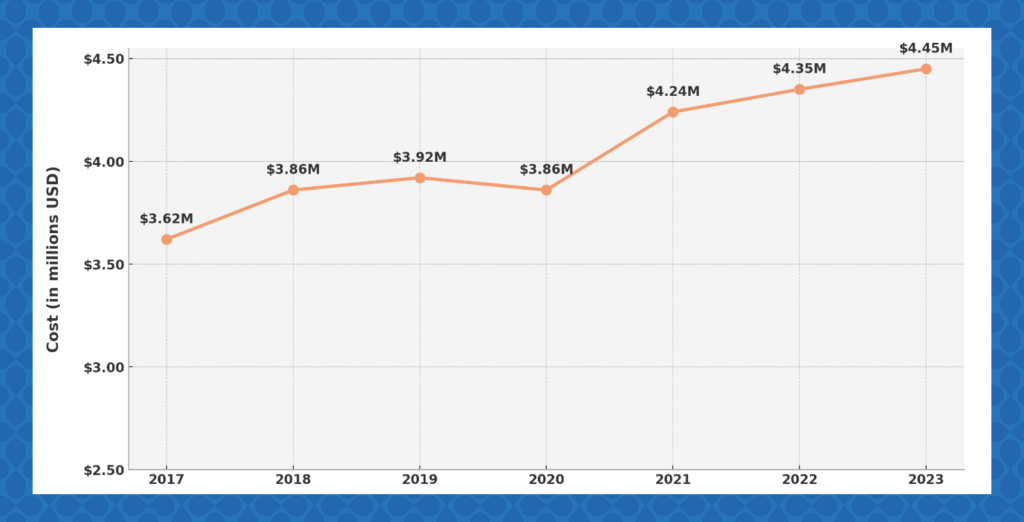
Currently, the average cost of data breach for companies is $4.45M, a 15% increase over 3 years. For businesses and accounting firms alike, the mere risk of such a loss is extreme. More importantly, a companies’ reputation can also face immense backlash, even resulting in it having to close. These stories are not rare by any means.
Examples of Accounting Cybersecurity Breaches
Sequoia Capital (2021)
Financial institutions like Sequoia Capital are often the targets of criminals seeking to hack financial data. This example was not as severe as it could have been, only one employee’s email was successfully hacked through a “wire diversion scam.”In fact, just one data breach can jeopardize customer and business financial data resulting in significant financial loss. Even more, Sequoia had to deal with informing customers and potential investors.
Capital One Data Breach (2019)
This is a prime example of how unguarded internal accounting processes can cause major damage to a company. One of Capital One’s own employees illegally accessed one of the Amazon Web Servers storing vital data and stole 100 million credit card applications. As a result, approximately 140,000 social security numbers were leaked, as well as 80,000 bank account numbers.
What about Small Business Data Breach?
You may think criminals only want to hack the financial data of enterprise size or large businesses? Not true. Small to medium-sized businesses are prime targets too, only the consequences can be more devastating. According to an Inc. article, 60% of small businesses fail within six months of a cyber attack.
Even if a business doesn’t close, the costs of a data breach can be immense. For example, an Oregon-based accounting firm, Gustafson & Co, experienced a massive data breach and was forced to pay $50K after 1,900 individuals were exposed.
Cyber Security for Accounting Firms: 6 Essential Practices
There are risks to your financial data both outside of and inside of your organization. Subsequently, it’s not hard to take control and get ahead of these threats. Preventing or at least mitigating data breaches starts with putting the proper protections in place. There is already evidence that with increased awareness of cybercrime and increased security investment, companies can protect themselves effectively. But, this comes with a dual focus on safe practices and technology. Start doing these financial security steps right now!
1. Know Your Threats
As an accountant, you face threats like hacking, ransomware, and phishing scams, but internal threats and errors are just as compromising. Accidental data sharing can occur easily with untrained staff, and there are multiple ways data relevant to the financial lifecycle can be misplaced. It’s critical to analyze how your individual organization handles data and create accountability into your actual accounting practices for proper data management.
2. Train Your Staff
As the accounting profession becomes more intertwined with IT and cloud accounting, protecting financial data will take precedent. Instilling a sense of ownership in financial data is a vital necessity. For instance, do this by educating your team on the growing threats and risks of a financial data breach and how to prevent ransomware attacks. In the same vein, accounting system security is critical not only for your accounting firm and your reputation but also for your customers. Accounting Seed values accounting security so much, we make it our mission to provide resources to help accountants and businesses protect their data. Check out our free guide and webinar.
3. Know Your Regulations
Some of your security threats may be covered within business, state, and federal regulations you must follow. This is especially the case if your accounting firm contracts with the federal government. These regulations protect you, your customers, and ensure proper accounting standards. Document these requirements and incorporate them into your reporting and accounting standards.
4. Design an Approval and Validation System
Your most trusted and experienced managers and approvers must take ownership. Establish which actions and data need to be looked over and approved by higher-level managers. Besides ensuring the most experienced and trustworthy staff members have the final authority on using data, this also helps protect your accounting firm from potential errors. Remember, accidental data sharing is common, and about 80% of data breaches are caused by internal human errors. Constructing an approval and validation system helps ensure no mistakes are made that would jeopardize your data.
5. Establish Security Requirements
Work with your team to identify risk factors to create a comprehensive financial security requirements list. Besides taking in specific accounting practices and regulations, examine your unique process to see where data slips may occur. As you collaborate, internal controls should be considered too. These play a big role in defining additional functionality you need from an accounting system.
6. Choose the Right Accounting System
The most critical step in accounting cybersecurity is choosing the right accounting system. The best plans and established financial security requirements mean nothing if you can’t implement them. Or, if you’re forced to implement these protections manually. The reality is that basic accounting security features like usernames and passwords aren’t enough anymore. To secure your accounting system against current cyber threats and ransomware attacks, you need a flexible system that has both strong encryption and automated internal security functions.
Keep Financial Data Secure with Reliable Accounting Software
Besides helping your accounting firm manage and analyze finances more efficiently and effectively, one of the core uses of accounting software is protecting your financial data. Remember, you’re not just protecting your firm, you’re protecting the identities and data of your clients. Investing in a secure accounting platform isn’t just necessary, it is a vital step to ensuring your company’s sustainability. Not to mention, your customers’ safety and well-being. But what constitutes a secure accounting system?
Three Core Areas Financial Data Security Features:
1. Natural Event Protection
Securing data through the cloud and with backups to ensure natural disasters and physical destruction or malfunction does not expose or lose data. The cloud has helped eliminate a lot of these threats, so make sure your financial data can be stored on the cloud and accessed virtually.
2. External Threat Protection
This refers to protection from hackers trying to hack financial data – your first line of defense. Strong, secure Application Programming Interface (API) is important to ensure the safety of your financial data as you connect it with other applications. Encryption and overall robust IT infrastructure is also critical to keeping hackers out.
3. Internal Threat Protection
This is your second, more intensive layer of defense which protects you from both external and internal intrusions. If an external threat breaks past firewalls or encryptions, they then have to contend with passwords, permissions, and user hierarchy. Things like passwords and usernames are pretty standard protections across various products, but they’re not enough. More in-depth features are needed to create an extra barrier against cyberthreats while also protecting your accounting data against potential internal errors or malicious activity.
Here are Some Core Features to Look for:
Two-Factor Authentication
Two-factor authentication lets you enable a second level of authentication for every login. You can also implement a two-factor authentication when a user is performing a specific function like examining billing reports or approving expenses.
User Permissions
User permissions let you clearly define what tasks users can perform, approve, and have access to.
Approvals
You can automate specific steps or sequences of events that require an official signoff on a record to ensure accuracy. The signoff can be linked to the desired authority to ensure data is accurate and secure, and that the current process is proceeding correctly.
User Role Hierarchy
Establishing a user hierarchy lets you dictate which specific user(s) can view or change specific components of accounts or records within the system, like reports. Roles determine user access to opportunities, cases, and contacts.
Validation Rules
Validation rules establish standards for recording and handling data. These security measures also ensure that only select users can do a certain process in the system. Based on business logic, validation rules can be set to prevent processes from being completed out of sequence.
Real-Time Event Monitoring
Real-time event monitoring helps you keep track of and monitor standard events in near real-time.
Audit Trail Functionality
Audit trail lets you track changes throughout the financial reconciliation process to maintain accurate, up-to-date information. This also lets you see exactly who is doing what in the general ledger, with project accounting, and every other aspect of the accounting process.
Object/Field Trail Functionality
Object/field trail functionality lets users view and document changes done to an object or a specific record within the object.
Workflow Rules
Workflow rules let you create and automate internal processes and procedural steps in orchestrating key accounting functions. This dictates how data is logged, accessed, processed, and used.
Secure Email Functions
Encrypt and safely send sensitive emails with accounting data involved. In Accounting Seed, you can utilize page layouts and Salesforce permissions to restrict users from viewing attachments too.
Learn about all things accounting cybersecurity in our free guide.
Protect Your Accounting Data Right Now with Accounting Seed
Accounting Seed has all the security features you need to fully protect your accounting data from any threats you face on the cloud. Our flexibility also lets you tailor these security features however best suits your individual needs. Keep your accounting data secure and you keep your organization and customers safe too, not to mention happy.
At Accounting Seed we’re focused on removing security concerns to give you the peace of mind to use your accounting data effectively for your organization. Schedule a free demo today to see how our solution protects your data from all the threats of tomorrow, and beyond.
A native Salesforce accounting app, Accounting Seed, provides a full 360-degree view of your business’ performance to help you and your team make the best decisions possible. Not on Salesforce? Our software can be customized to work with any system you have through a reliable connection.
See Accounting Seed in action
Get a close-up view of how accounting on Salesforce can eliminate the need for costly integrations—and silos of mismatched information—by sharing the same database as your CRM.



